As organizations increasingly rely on cloud infrastructure, securing resources while maintaining connectivity becomes a priority. In Microsoft Azure, Service Endpoints and Service Tags offer effective ways to control and simplify network traffic management. In this post, I’ll walk you through what they are, why they matter, and how to implement them.
📌 What are Azure service endpoints?
A Service Endpoint extends your virtual network’s private address space to Azure services over the Azure backbone network. This allows secure, direct connectivity to services like Azure Storage, Azure SQL Database, and others — without requiring public IP addresses. Usually, the service is created and accessed via public internet – for example Azure Blob Storage is accessed via the url endpoint. However, by using service endpoints, we access the resource as if it was in the same VNET rather than accessing it via public internet.
Key Benefits:
- Improved security: traffic never leaves the Azure backbone
- Easy configuration without VPN or ExpressRoute
- Supports network security group (NSG) rules for fine-grained control
Let’s say you have a storage account and you want to allow access to a file share only from given VMs – service endpoints are created exactly for this scenario:
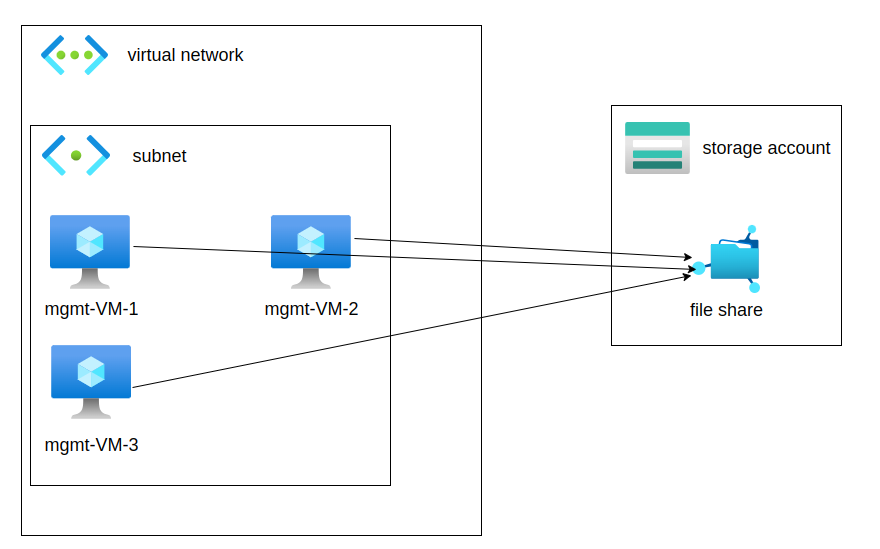
In the example above, three VMs located in subnet inside of virtual network are given access to a file share inside of a storage account. As I show later in the post, there is a option in storage account to allow access only from selected VNETs -> by selecting this option, the service endpoint is automatically created.
🔧 How to create service endpoints
Note: even though you can create service endpoints manually as shown below, it is not necessary as they are created automatically when you enable access to given Azure service. If you do not want to create them manually, head to the next section of this blog.
Let’s set up a Service Endpoint for Azure Storage as an example:
Steps:
- Go to your Azure Virtual Network
In the Azure Portal, navigate to your Virtual Network resource.
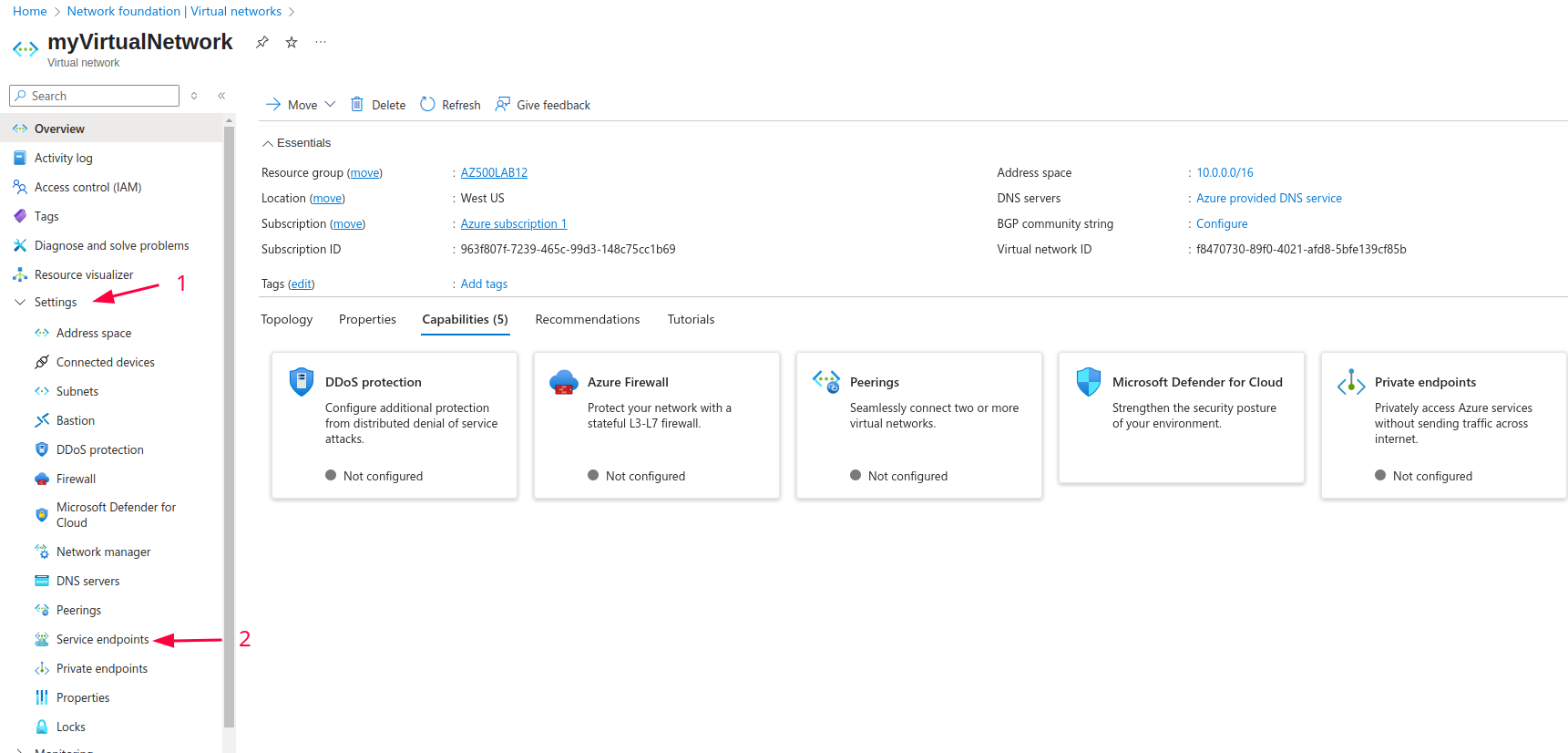
- Select ‘Service Endpoints’ under Settings and click on + Add.
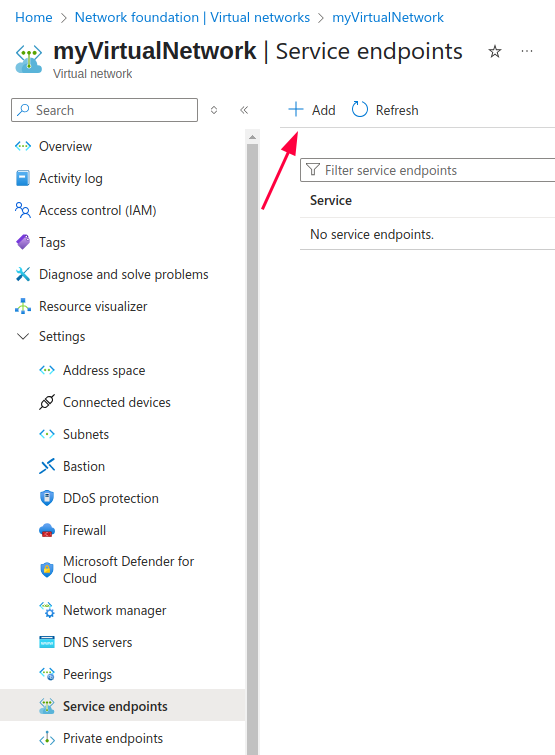
- Choose the Azure Service
SelectMicrosoft.Storagefrom the list.
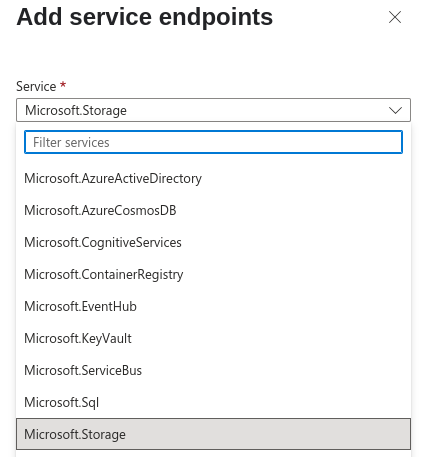
- Select the Subnet
Pick the subnet you want to enable the endpoint for.
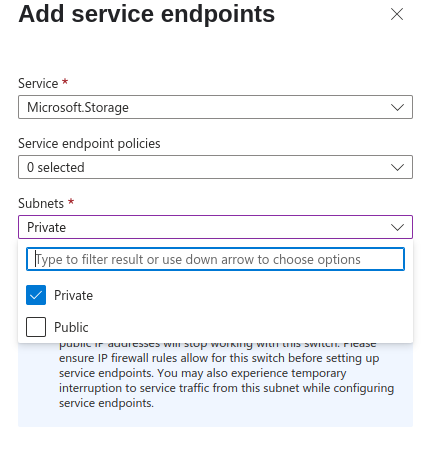
- Click Add
Done! Now your subnet has direct, secure access to Azure Storage.
Example via Azure CLI:
az network vnet subnet update \
--resource-group AZ500LAB12 \
--vnet-name myVirtualNetwork \
--name Private \
--service-endpoints Microsoft.Storage🔧 How to use service endpoint to allow access to storage account
- Go to your storage account -> head to Security + networking -> Networking
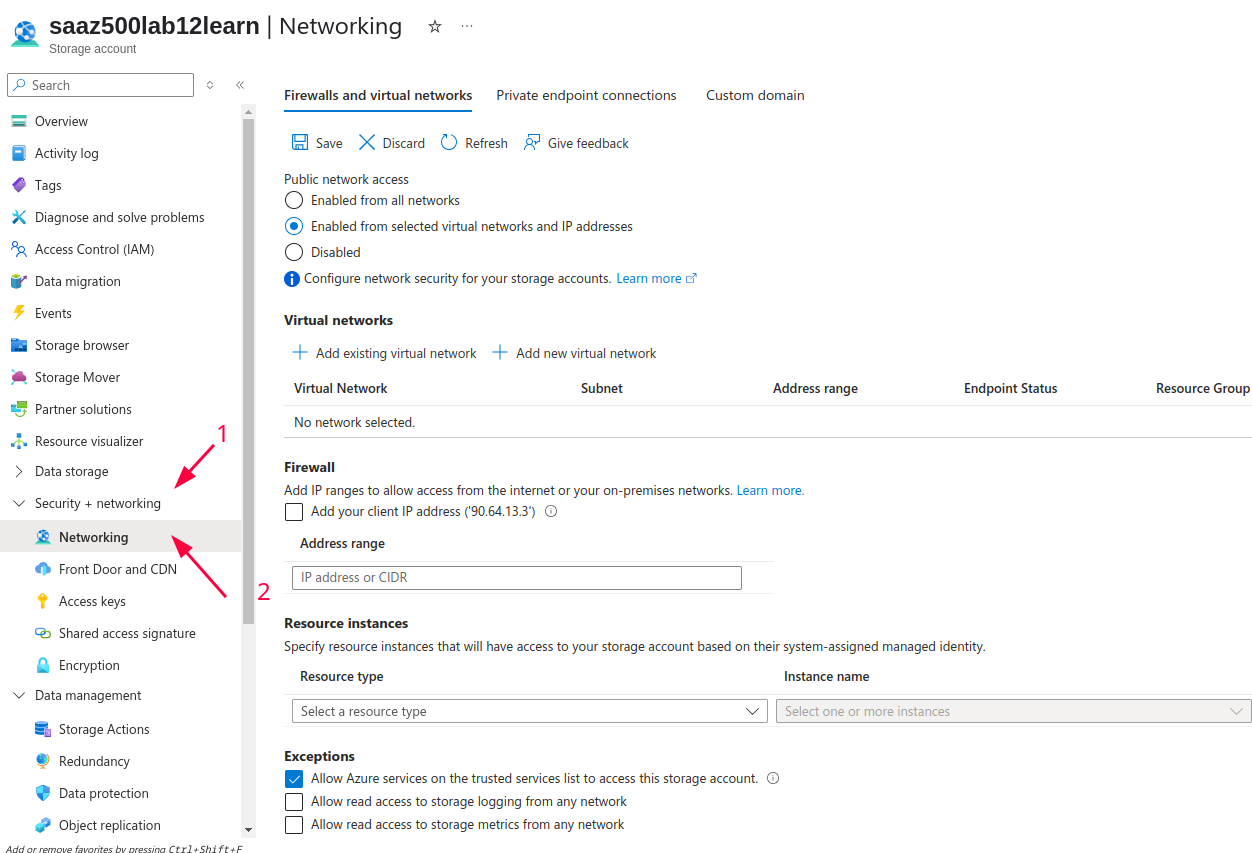
- Under virtual networks click on Add existing virtual network and fill out the details about your virtual network as well as subnet from which you want to allow an access.

Allow access via Azure cli
If you prefer using cli you can also allow access access to storage account via following steps:
- Change the default action for network access:
az storage account update \
--resource-group "AZ500LAB12" \
--name "saaz500lab12learn" \
--default-action Deny- Add a VNet/Subnet Rule to Allow Access
az storage account network-rule add \
--resource-group "AZ500LAB12" \
--account-name "saaz500lab12learn" \
--vnet-name "myVirtualNetwork" \
--subnet "Private"Now, the storage account is reachable only from the “Private” subnet of “myVirtualNetwork” VNET. The traffic is traversing only through Azure backbone network.
📌 What are Azure service tags?
A Service Tag is a predefined label representing a group of IP address prefixes for a given Azure service. It simplifies NSG rule management by allowing you to reference a service by name rather than individual IP addresses.
Key Benefits:
- Reduces administrative overhead
- Keeps NSG rules up to date automatically as Azure’s IP ranges change
- Makes NSG rules more readable and maintainable
If you want to see a full list of Azure IP Ranges and Service Tags visit this link. The link contains json file with Azure resouces and their corresponding IP ranges. For example, if you want to get a list of IP prefixes for Azure App Service located in central Australia region you can use the jq tool and execute the following command:
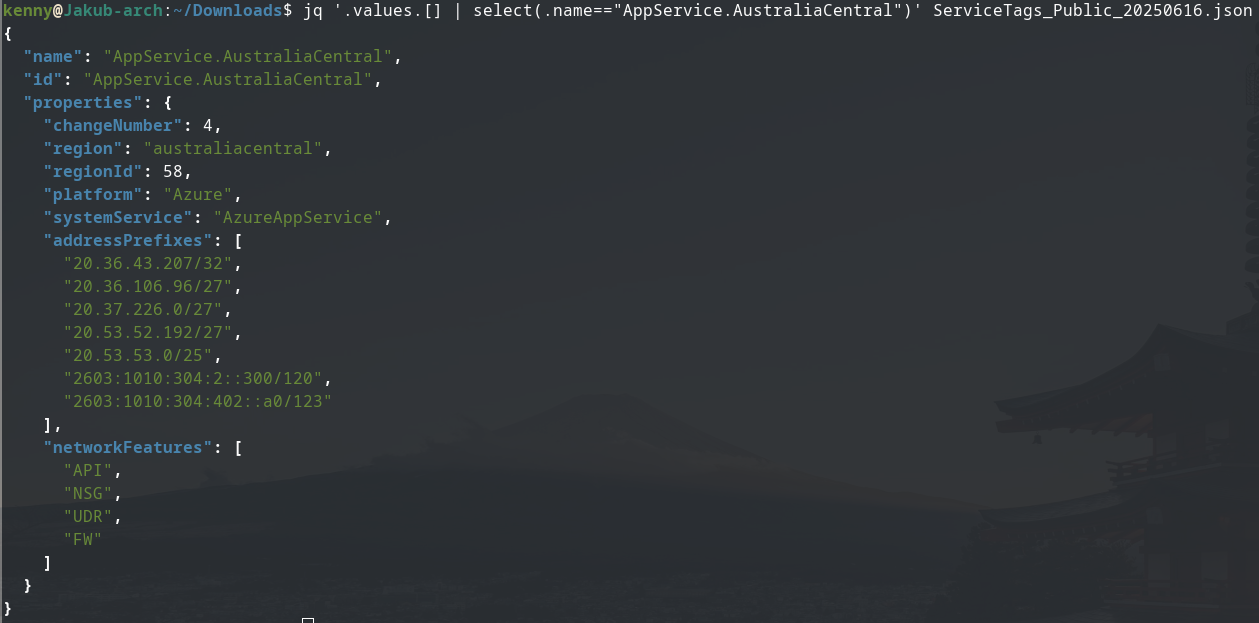
From the result above, I was able to get both the Ipv4 and Ipv6 prefixes for App Service located in australia central region.
🔧 How to use service tags in NSG Rules
To control traffic to or from Azure services, use Service Tags in your Network Security Group (NSG) rules.
Example: Allow outbound traffic to Azure Storage:
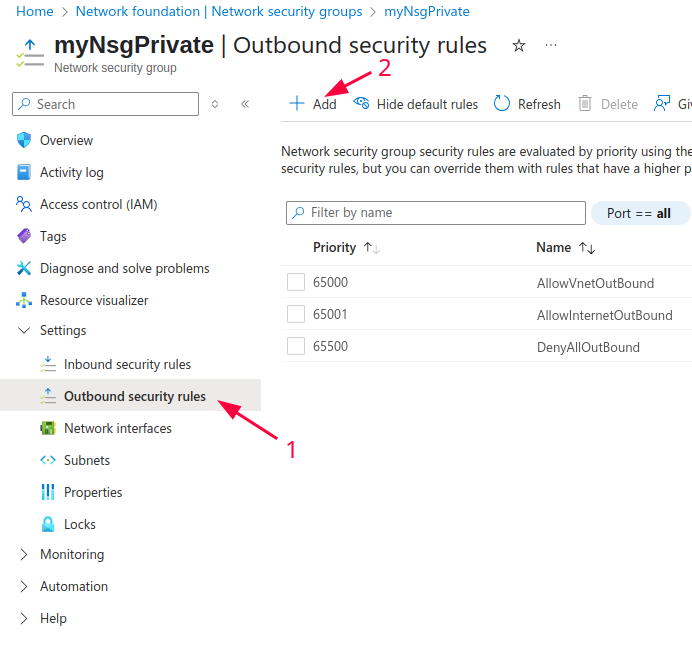
- Go to Network Security Groups in the Azure Portal. Choose your existing NSG.
- Select Outbound Security Rules → + Add
- Set:
- Destination: Service Tag
- Destination Service Tag:
Storage - Port:
443 - Protocol:
TCP - Action:
Allow
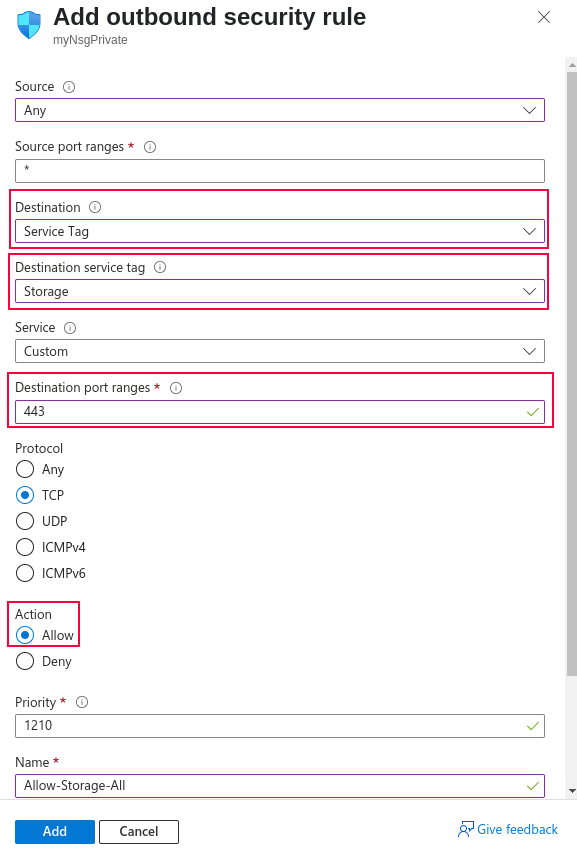
- Click Add.
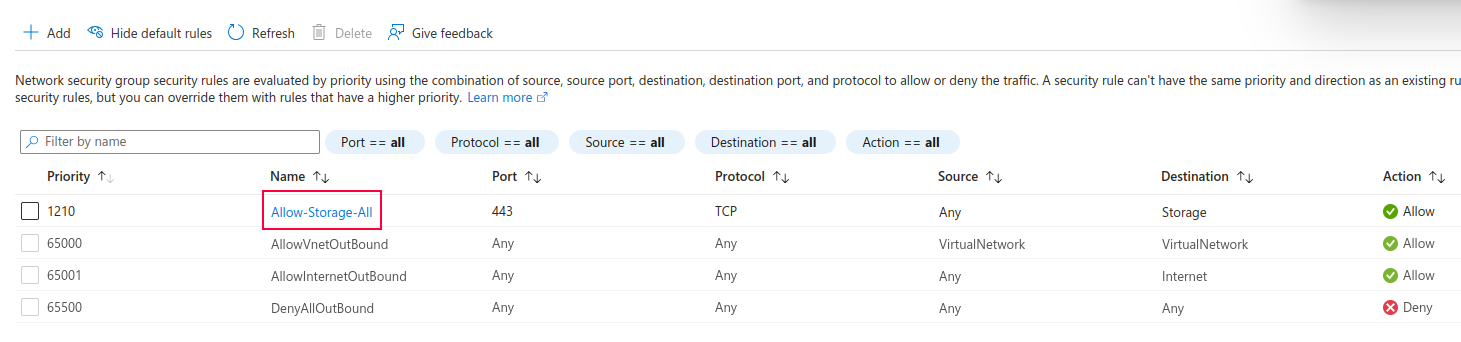
After you add the rule, it becomes visible in the portal:
Example via Azure CLI:
az network nsg rule create \
--resource-group MyResourceGroup \
--nsg-name MyNSG \
--name AllowStorageOutbound \
--priority 1000 \
--direction Outbound \
--access Allow \
--protocol Tcp \
--destination-port-ranges 443 \
--destination-address-prefixes Storage \
--source-address-prefixes '*' \
--description "Allow outbound to Azure Storage"
📊 Service tags vs service endpoints – when to use which ?
| Use Case | Choose |
|---|---|
| Secure service access within Azure backbone | Service Endpoints |
| Simplify NSG management for Azure services | Service Tags |
| Maintain private IP access while avoiding public IP dependencies | Service Endpoints |
| Centralize and future-proof NSG rules | Service Tags |
✅ Conclusion
Service Endpoints and Service Tags are essential tools in any Azure architect’s kit, helping you enhance security, optimize network traffic, and simplify management. Whether you’re building secure enterprise solutions or migrating workloads to the cloud, these features streamline your Azure network configuration.
