Azure RBAC roles is probably the most important part of Entra ID and IAM in general. By delegating access to resources by using roles we improve security, robustness and management in general. Roles can be assigned to service principal(user, enterprise app, device) or to existing group.
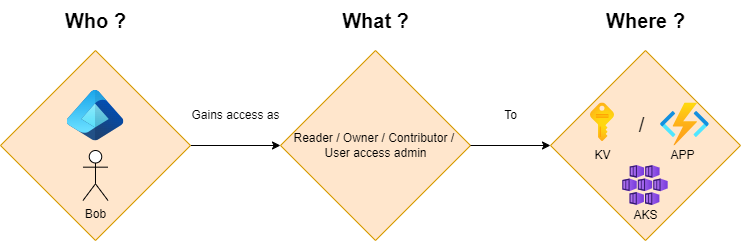
The good way to think about azure roles is to ask ourselves 3 questions:
- Who ? – who will we gain access. It can be already mentioned service principal or group.
- What ? – what access will we allow ? It can be for example reader or owner.
- Where ? – what is the scope for the access ? It can be to certain web app instance, to resource group or even to subscription itself
When we answer the 3 questions above, we should be able to assign the right permissions to the right scope. In this example, we assign to the user Bob located in Entra ID role we choose – either reader, owner, contributor or user access admin and we assign it to the right scope – either to subscription, function app or aks, but the list goes on.
Azure roles
This role assignments control the access to your Azure resources.
There are 4 main roles in azure: reader, owner, contributor and user access admin. These are so called built-in RBAC roles. However, if the mentioned roles do not fulfill your needs, you can always create the custom ones.
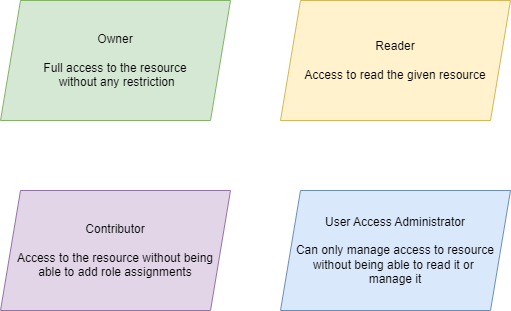
Generally speaking, the mentioned 4 roles shall be enough to cover most of your IAM(identity access management).
Assign Azure role to user
In this example, I will use the existing storage account in order to show you how to assign role:
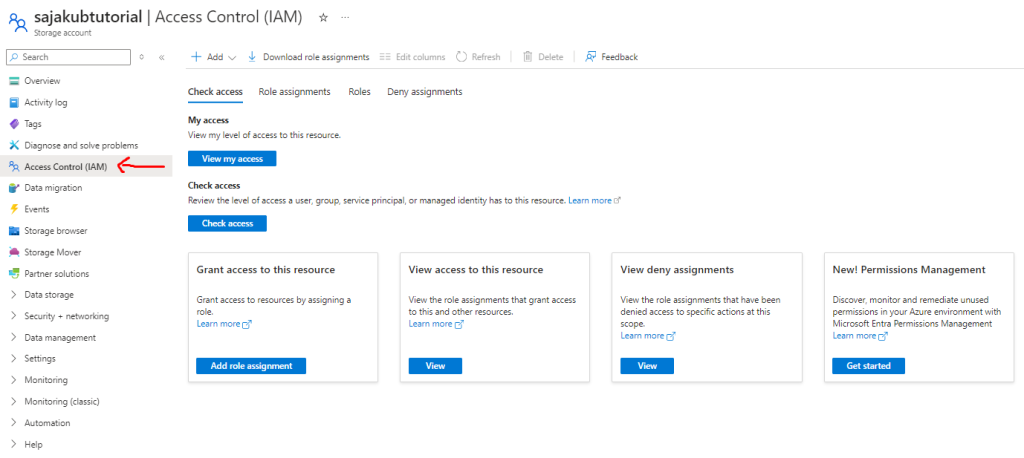
- First go to your storage account and head to Access Control:
- After that click on Add -> Add role assignment:
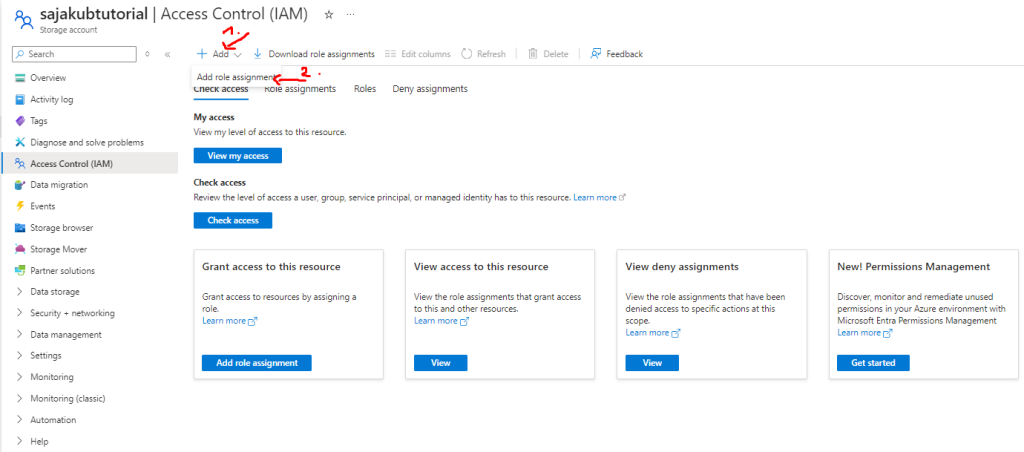
- From there go to Role tab, click on Privileged administrator roles and choose the Contributor role:
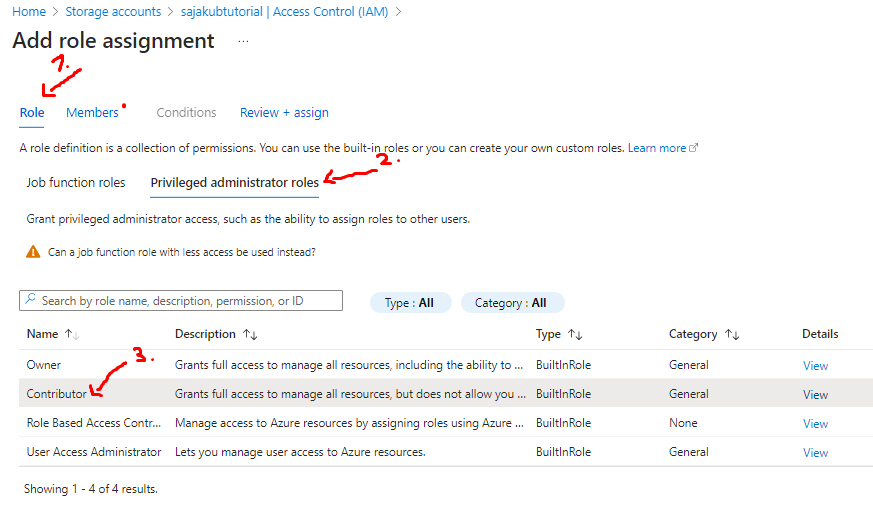
- After that head to Members tab, click Select members, choose your user and click on Select:
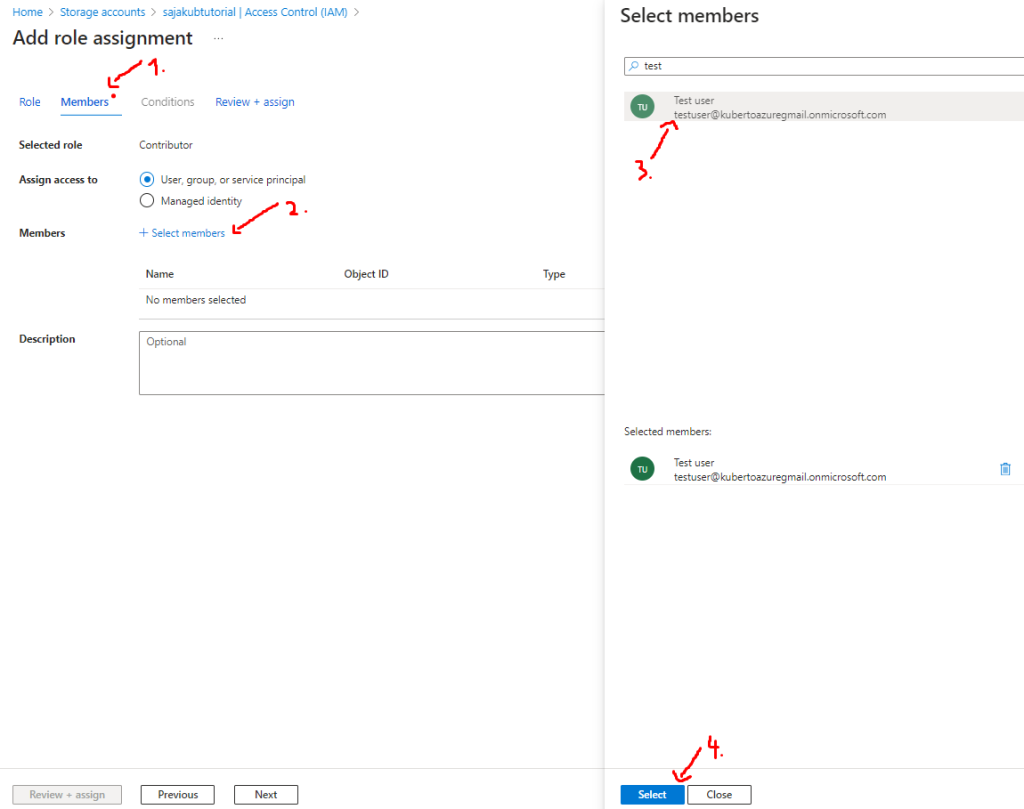
- As the last step, head to Review + assign tab where you can double check the assignment and after that click on Review + assign button:
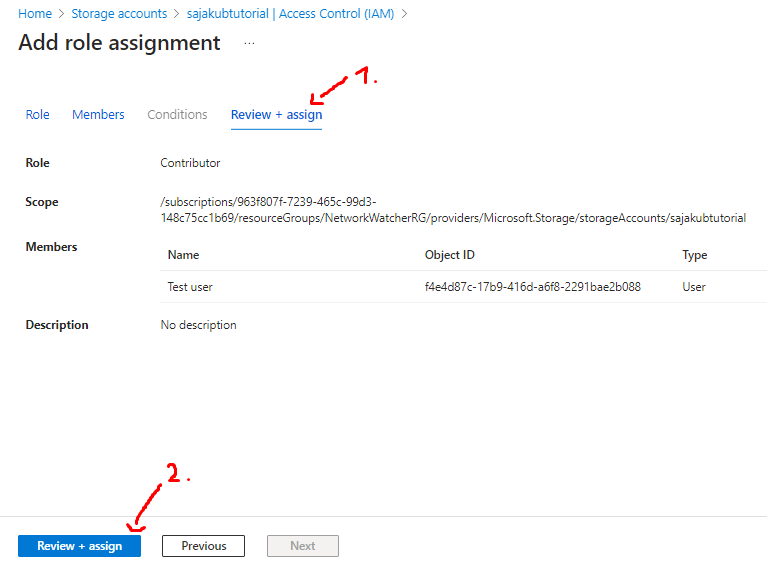
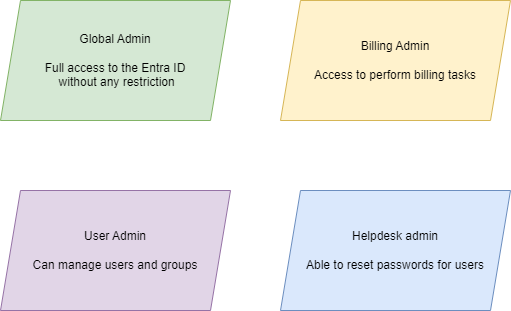
Entra ID roles
Entra ID roles provide a way to manage access to identity objects inside our Entra ID. In layman terms, it’s roles by which we can view, edit and manage entities in our Entra ID such as users, enterprise apps, groups, etc.
Compared to Azure roles which are focused on resources such as virtual networks, function apps, etc. the Entra ID roles focus on Entra ID located in tenant.
Assign Entra ID role to user
In the second example, I will use assign my test user the User Admin role:
- First head to your portal and go to Microsoft Entra ID:
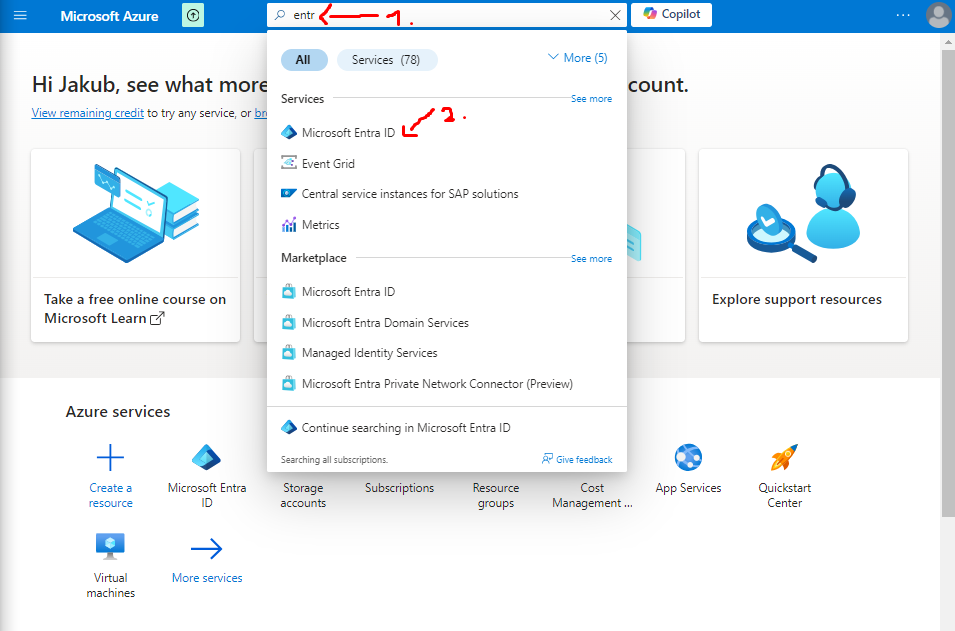
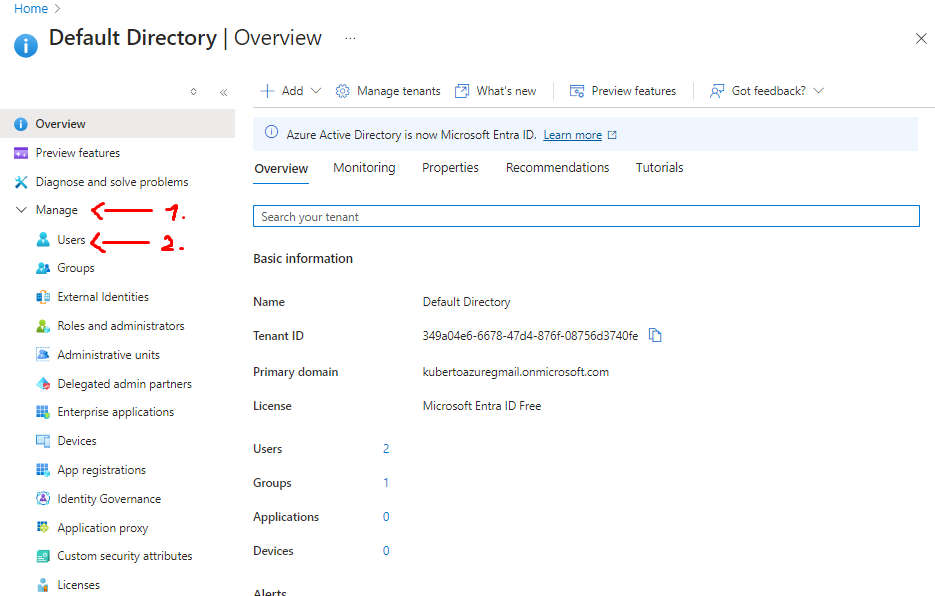
- After that head to Manage -> Users:
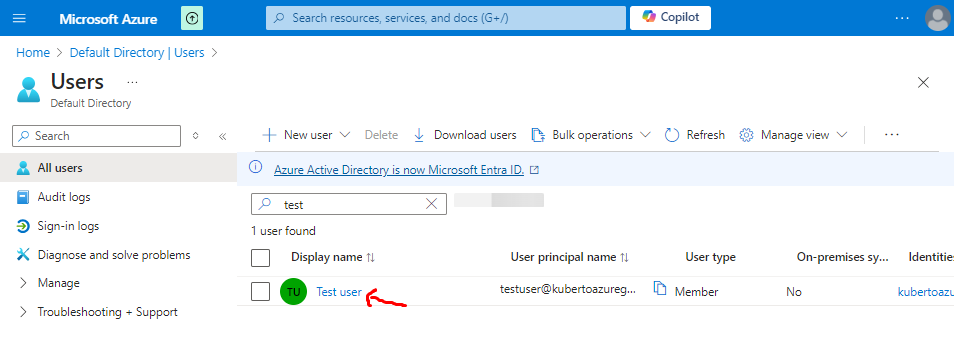
- Choose the user to who you will assign the role (in my case it’s Test user):
- From there go to Manage -> Assigned roles:
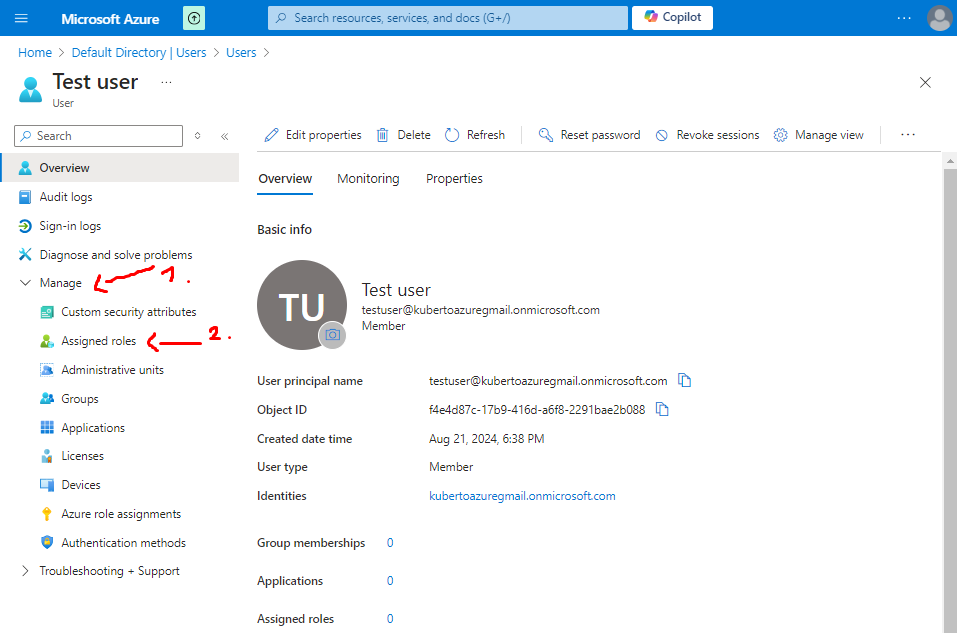
- Click on Add assignments, search for User Administrator, click on the checkbox and finally click on Add:
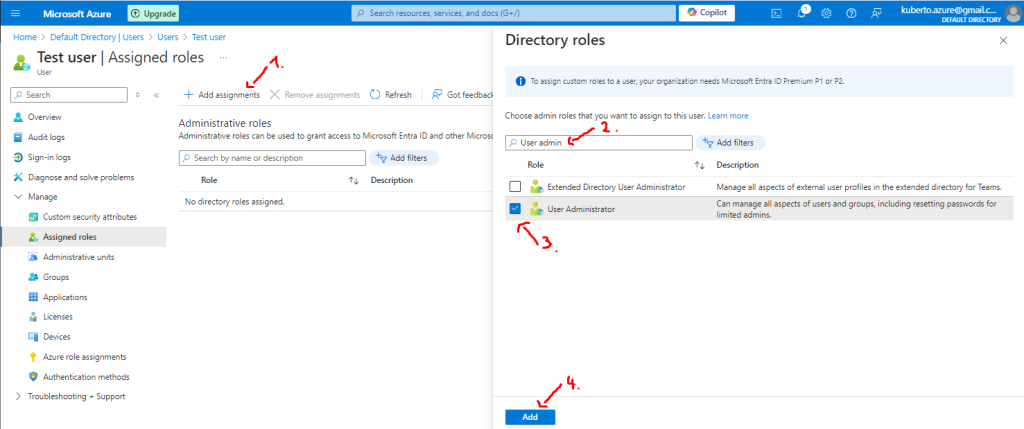
After the last step, you should the notification about successfully added assignment.
Azure roles vs Entra ID roles
| Azure roles | Entra ID roles |
| Manage access to azure resources | Manage access to Entra ID entities |
| Have pre-defined built-in roles | Have pre-defined built-in roles |
| Possibility to create custom roles | Possibility to create custom roles |
| Can be assigned to multiple levels (subscription, resource group, web app, etc.) | Can be assigned to tenant level |
Conclusion
In this tutorial, I explained to you what are azure RBAC roles and how to use them. We went through azure roles as well as entra ID roles. RBAC is nowadays very enforced IAM solution and it is being applied to multiple aspects of cybersecurity, not just the azure. For example, very popular kubernetes also uses RBAC roles in order to enforce security and IAM in general.

